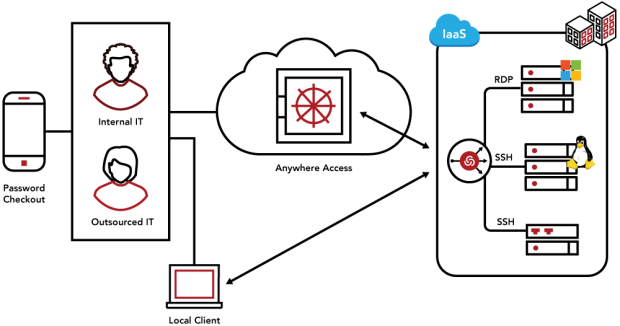
Secure and Manage Privileged Access with a Radically Different Approach
Centrify is redefining the legacy approach to Privileged Access Management (PAM) with cloud-ready Identity-Centric PAM founded on Zero Trust principles. This allows establishing trust, and then granting least privilege access just-in-time based on verifying who is requesting access, the context of the request, as well as the risk of the access environment.
| 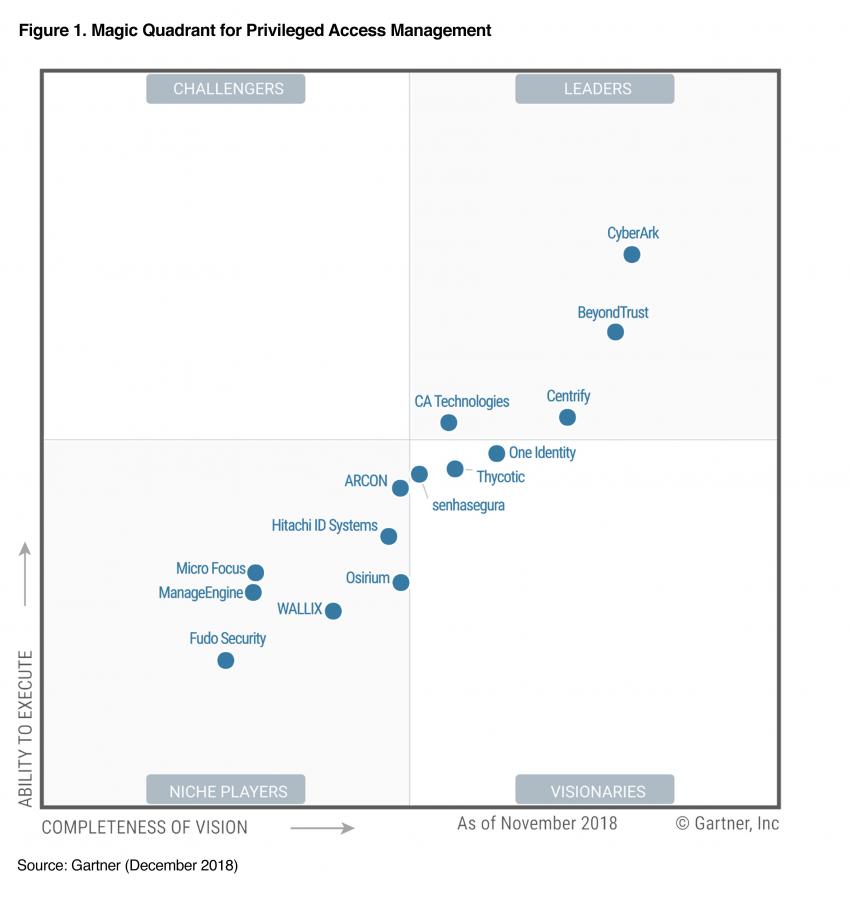 |
PRIVILEGED ACCESS MANAGEMENT
ZERO TRUST PRIVILEGE SERVICES
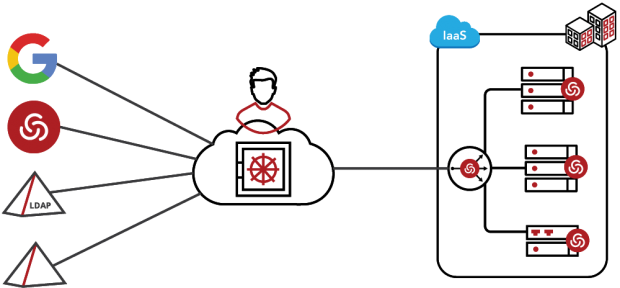
A Radically Different Approach to Privileged Access Management Centrify is redefining the legacy approach to Privileged Access Management (PAM) with cloud-ready Zero Trust Privilege to secure modern enterprises and stop the leading cause of breaches — privileged access abuse.
 |
|
| 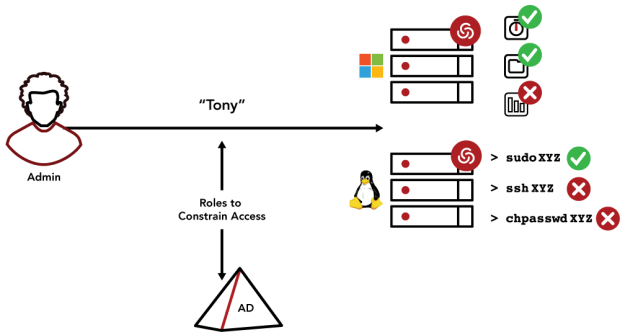 |
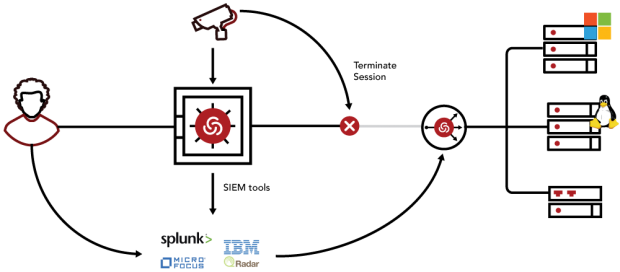 The Centrify Audit and Monitoring Service allows customers to fulfill their compliance mandates through auditing and reporting as well as shut down any dangerous workarounds by putting host-based monitoring in place. |
|
| 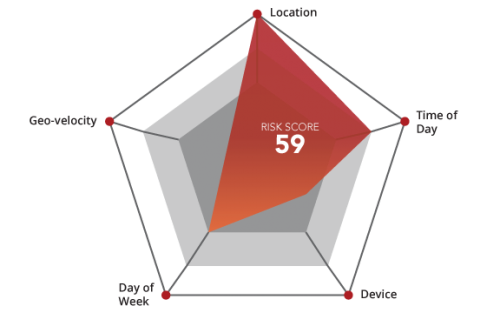 |
Trusted by over 2,000 Organizations, Worldwide